SecOps Vulnerability Response Lifecycle
SecOps Vulnerability Response Lifecycle streamlines vulnerability management by prioritizing vulnerabilities based on asset, severity, exploitability, and threat intelligence. ServiceNow Security Operations use Vulnerability Response to empower IT and vulnerability teams.
Using a unified workspace, they can use automated tools to swiftly address risks. Eradicate bottlenecks and inefficiencies by replacing manual processes, spreadsheets, and emails with automated, scalable workflows for faster remediation.
This guide includes a dashboard view of business services at risk, and how they are trending, with actionable insights and proven methodologies to strengthen your defenses. CISO Dashboard tabs put everything in one view.
Reimagine SecOps Vulnerability Response Lifecycle Demonstration
The Vulnerability Response Process:
The purpose of the vulnerability response process is to guide Remediation Tasks through a structured journey, starting from ‘Open’ Vulnerable Item Records and culminating in ‘Closed’. This process, symbolized as a chevron, provides flexibility, allowing for both forward and backward movement, and at times, even the option to bypass specific states.
Dynamic State Management from Integrations
By integrating with vulnerability scanners and accessing supporting archives, the platform gains a wealth of detailed vulnerability information. When created in ServiceNow VR, both Remediation Tasks and Vulnerable Items automatically adopt the default ‘Open’ state. Additionally, documentation linked from the integration maintains a comprehensive library of third-party vulnerability entries.
How To Clinic on SecOps Vulnerability Response Lifecycle
These entries are presented alongside scanner findings in the Vulnerable Items table, enhancing the view and enriching vulnerability data within the CMDB. Reopening a vulnerable item record from a non-open state resets it to this initial value, signifying specific tasks or items that require immediate attention.
ServiceNow Vulnerability Response State Flow
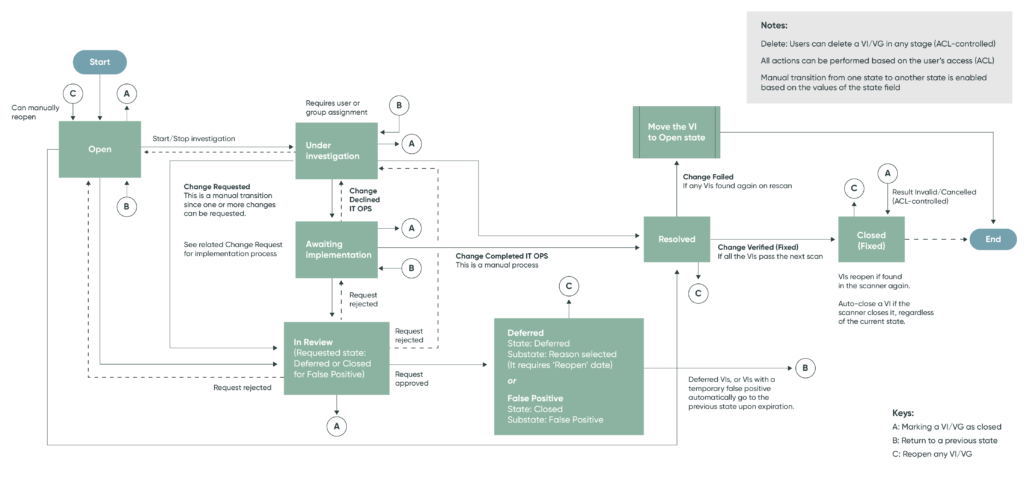
Open:
The Open state marks the starting point of a Vulnerability record’s journey. When established in ServiceNow VR, both Remediation Tasks and Vulnerable Items automatically set to this default state. Moreover, if a vulnerable item record is reopened from a non-open state, it returns to this initial status. This state serves as a clear indicator for specific tasks or items that require immediate attention.
Vulnerability Workspace Demo for SecOps Vulnerability Response Lifecycle View
Under Investigation:
As teams assume ownership of tasks and their corresponding Vulnerable Items, the task state transitions to ‘Under Investigation’. This signifies active engagement and ownership responsibility for addressing potential risks. In this phase, teams meticulously scrutinize vulnerability findings, assess impacts, and devise effective risk mitigation strategies.
Awaiting Implementation:
Following the acknowledgment of routed vulnerability findings, this state indicates a plan to address identified risks. A robust risk mitigation plan is now in motion, undergoing thorough due diligence and mandated procedures for a seamless rollout.
Deferred:
In situations involving mission-critical systems or substantial reliance on third-party vendors, there may arise a need for additional time in the risk mitigation planning process. This state indicates an ongoing plan that cannot be implemented within the current timeframe. Typically, teams submit a request to postpone risk remediation tasks to a specific date, awaiting approval.
Resolved SecOps Vulnerability Response Lifecycle:
Responsible teams affirm the completion of risk mitigation activities, marking the conclusion of remediation efforts. This validation is of utmost importance before officially closing a task. Usually, this verification occurs during the subsequent scan, confirming the absence of these vulnerabilities.
In Review:
When teams request the transition of tasks into a non-open state, these requests are queued for approval. This state clearly indicates that tasks are in a pending state, awaiting manual movement approval.
Closed:
As teams actively resolve vulnerabilities, they prompt third-party scanners to acknowledge their absence. This state unequivocally affirms the absence of risks. Furthermore, it may indicate manual closure following an approval process, complete with an appropriate resolution code. Additionally, this state adeptly handles false positive vulnerabilities, ensuring they remain inactive and preventing any reactivation by the scanner.
Resources Related to SecOps Vulnerability Response Lifecycle
- FAQs: ServiceNow Governance Risk Compliance
- Glossary: Security-Operations GRC
- GRC Framework CIO Insight
- itSMF Executive Panel on Modern Critical Situation
- Knowledge Article View – Now Support Portal (servicenow.com)
- Remediation Workspace (servicenow.com)
- Rescan records and remediation tasks in the Vulnerability Manager Workspace (servicenow.com)
- Rescan Tenable.io and Tenable.sc vulnerable items from VR workspaces (servicenow.com)
- Vulnerability Response remediation overview (servicenow.com)
- Vulnerability Response Workspaces (servicenow.com)
- View the dashboards in the Vulnerability Manager Workspace (servicenow.com)

-
Getting Started
- AI: ServiceNow Virtual-Agent Chatbot
- BMC Remedy ITSM Reference
- Burp Suite Professional & Web Security Process
- COE for Human Resources
- Conduct A Windows-Security Scan
- Employee Journey Management ServiceNow
- Getting Started: Engagement Manager
- Introduction to Knowledge Management
- Knowledge Categorization "Find-ability"
- One-IT: Effective Ticket Handling
- Productivity Tips for Knowledge-Users
- Productivity: Service Operations Workspace
- Quick Start Guide
- Service Catalog Order Guides
- Your Next Steps
-
- Advanced Program Management
- AI: ServiceNow Virtual-Agent Chatbot
- Artificial Intelligence A-Z Glossary
- Business Process Optimization Reviews
- Category Hierarchy and Tabs Layout
- Employee Journey Management ServiceNow
- GE Change Acceleration Process
- GRC Managed Risk
- Overview: Employee Center Pro
- Productivity: Service Operations Workspace
- Proper Ticket Handling Imperative
- Public Sector Digital Services
- RIDAC: Strategic Portfolio Management
- SOX Control-Management and Attestation
-
- Articles coming soon
-
FAQs
- Best of ServiceNow Vancouver
- Chat GPT FAQS
- DevOps & Change Velocity
- Enhancing End-User Service Experience
- FAQs: Governance Risk Compliance
- How-To Import ServiceNow Stories 🚀
- Knowledge Categorization "Find-ability"
- Role of CMDB-Management Service-Owner
- Service Catalog Process FAQs
- ServiceNow IRM SOX FAQs
- Strategic Portfolio Management FAQs
- Ticket Handling Infographic FAQs
- Understanding Clop Ransomware Mitigation
- Vulnerability Response Workspace Module
- Washington ESC or Knowledge Portal?
-
- AI & GRC Defense Against Security-Data Breach
- AI and Improved Knowledgebase-Search
- AI Revolutionizes Service Management
- AutomatePro AutoTest Custom-Testing
- AutomatePro AutoTest: Getting Started
- Best of ServiceNow Vancouver
- CMDB Health Dashboard
- Comparing ServiceNow-Strategic-PM to Microsoft-PM
- Demystifying Taxonomy Categorization
- DevOps & Change Velocity
- Efficient Workday to ServiceNow Integration
- Email-to-Incident is Costly Inefficiency
- Enhancing End-User Service Experience
- Financial Services Operations
- Gamifying ITSM Excellence
- GRC Industry Reference Matrix
- Introducing Security Incident Response
- Role of CMDB-Management Service-Owner
- Service Catalog Process FAQs
- ServiceNow Executive Reporting Approaches
- ServiceNow Virtual Agent Chatbot
- SPM Gantt Chart Presentation
- Strategic Portfolio Management FAQs
- Vulnerability Response Test Plan
- Vulnerability Response Workspace Module
- Washington ESC or Knowledge Portal?
- Show Remaining Articles11 Collapse Articles
-
Glossary Reference
-
Blog
- 2021: VP Harris Inauguration Elevates Diversity and Executive Leadership
- 5-Star ITSM Solutions
- 5-Step Policy-Compliance Risk Management
- AI & GRC Defense Against Security-Data Breach
- AI Revolutionizes Service Management
- AI: Knowledge Centered Support
- ChatGPT Ethics and FTC
- CMDB Corporate Governance for Publicly Held Companies
- Community Crisis Resource Reference List
- Covid Cyber Employment Fraud: $Millions in Job Fraud, $Billions in Unemployment Fraud. Recruiters and Jobseekers Paradigm shift
- Does Post Covid Demand, "Evolve or Fold" Data Strategy?
- Financial Services Operations
- Freshwork's Multichannel vision for FreshService (ITSM)
- Gamifying ITSM Excellence
- GRC Industry Reference Matrix
- Imperative: Governance Risk Compliance
- Jobs n Career Success: Employment News
- Microsoft Teams Tripping Transcription Tenancy.
- Predictive Intelligent Situational Awareness
- Remedy to ServiceNow Migration
- Review and Approve Knowledge
- ROI: Demand AI Service Management
- Top Trends in Project Management
- Uber's Call Center Security Social Engineering Massive System Breach
- Vulnerability Remediation RACI
- Walk Up Experience- Design-To-Deliver
- World Talent Economy Forum on Global Competitiveness
- Show Remaining Articles12 Collapse Articles
-
Healthcare
-
Workday
-
Network Connectivity Solutions
-
Business Process Methodologies

