Understanding Clop Ransomware Mitigation
Understanding Clop Ransomware Mitigation requires careful attention due to its dangerous nature as a file-encrypting virus. This malicious software actively seeks out unprotected systems and encrypts saved files by adding the “.Clop” extension. Various exploitation methods are known.
Understanding Clop Ransomware Mitigation Exploit 1: Clop Technical Support Scam
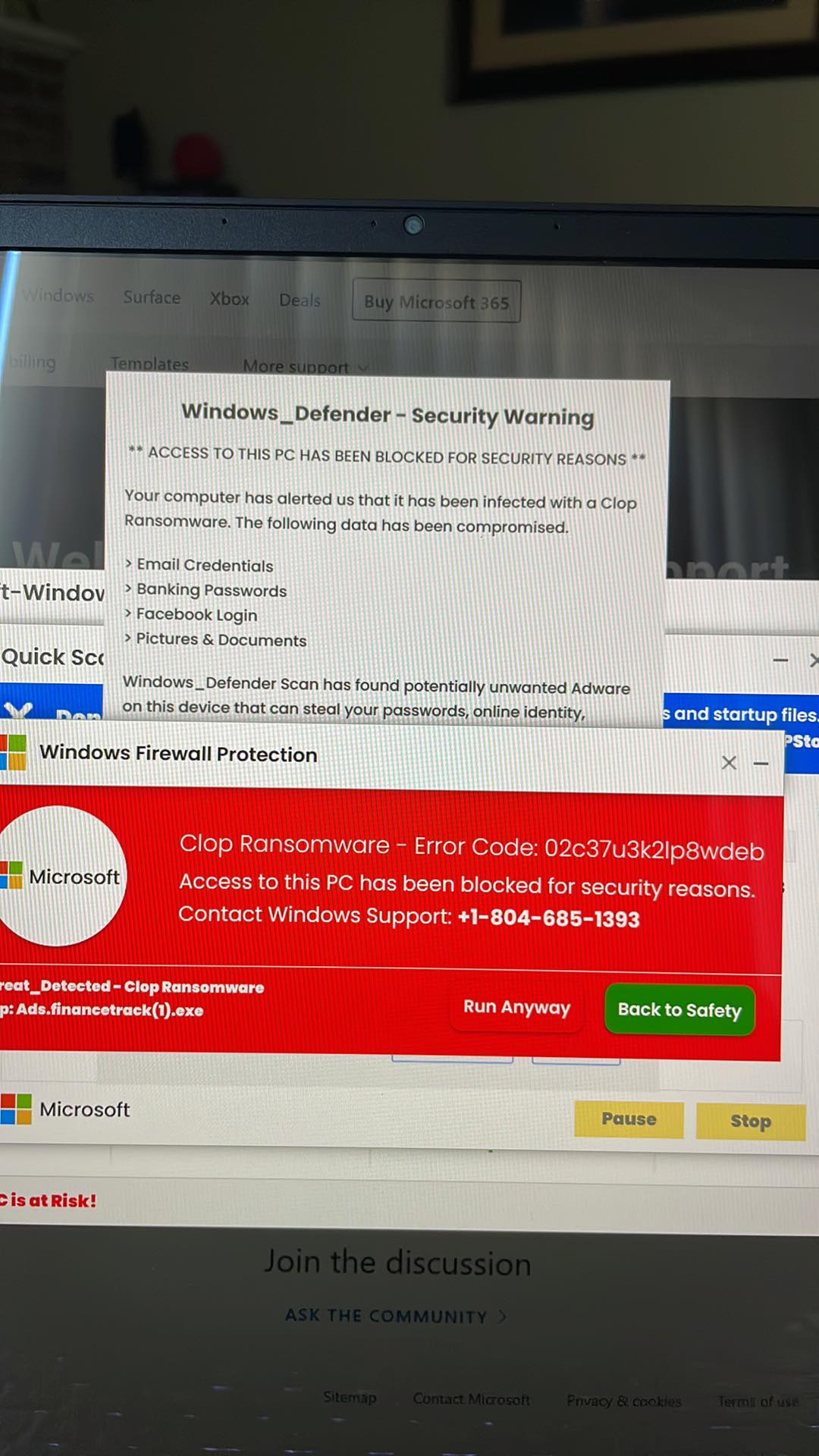
If you receive the Technical Support, it comes as a Pop-Up Scam that attempts to exploit with Cheap Scare Tactics. It looks like it’s from Microsoft. It has the familiar Microsoft Windows logo; it references the known Microsoft Windows Defender, and it is presenting a very realistic looking urgent detected Security Warning. It is colored ‘red’ a psychological tactic that subconsciously make you “feel” its urgency. It gives you a list of all of your “personal data that has been “compromised”.
Your mind is meant to seize on the risk of loss of personal data, banking and financial data, and your personal photos and documents. It then warns that you additionally have adware running that is going to steal more.
It tells you to click to go ‘back to safety’ in green and call the windows support number. Slow down and become very deliberate when someone is rushing you to commit an urgent action, particularly with technology.
Do not take the click or call bait.
Clop ransomware mitigation demands vigilant handling due to its perilous traits as a file-encrypting virus. This malware actively targets unprotected systems, encrypting stored files with the “.Clop” extension, using various exploitation methods.
When encountering the Technical Support pop-up, remain cautious of its deceitful nature, aiming to exploit users through manipulative scare tactics. It impersonates Microsoft, employing familiar elements like the recognizable Microsoft Windows logo and references to the widely-known Windows Defender. This cunning ruse presents an alarmingly convincing “urgent detected Security Warning,” strategically highlighted in red to trigger a fabricated sense of urgency.
The message lists compromised “personal data,” including banking info, personal photos, and documents, designed to evoke concern over potential loss. It further exploits psychological tactics by emphasizing the risk of additional adware invasion, aiming to steal more information.
Resist the temptation to click “Back to Safety” or “Run anyway,” as these options can lead to unintended consequences.
Moreover, it’s crucial to refrain from dialing the number listed in the message, as it’s part of the deception and could lead to further exploitation.
If you are referring to a message that appears on your computer screen claiming that your computer is infected with Clop ransomware and asking you to contact fraudulent support lines, then it is a technical support scam.
Do take these actions on the affected computer.
For effective mitigation of Clop ransomware, proactive steps are vital. Follow these actions on the affected computer to safeguard your data and system integrity:
- Capture Evidence: Take a photo of the message displayed on your computer, especially the phone number provided. Beware that the telephone area code 804 has a notorious history for fraud, robodials, and scams.
- Isolate Your System: On the compromised computer, perform the following steps:
- Shutdown your computer.
- Disconnect it from the network to prevent further spread of the threat.
- Enter Safe Mode: Restart your computer while taking these steps:
- During the normal boot-up process, press the F8 key every two to three seconds.
- Once a new menu appears, select “Safe Mode” and press Enter.
- Activate Microsoft Antivirus: While in Safe Mode, secure your system by:
- Accessing Windows Security settings.
- Navigating to Virus & threat protection > Protection history.
- Let Windows Defender Antivirus perform its functions, automatically detecting, removing, or quarantining malware.
- Reboot and Verify: Restart your system as usual. Confirm that it operates smoothly without any signs of ransomware intrusion.
- Seek Assistance: Should you encounter issues and require support, reach out to Microsoft Support using this link.
Instructions for reporting a phone scam.
Take swift action to counter phone scams, particularly with telephone area code 804. Follow these steps on your phone or another computer to report a potential scam:
- Validate the Number: Given the notoriety of telephone area code 804 for scams, it’s crucial to validate any suspicious number. You can do this by:
- Utilizing the National Phone Number Registry to search for the number in the affected system popup message: 8046851393 / 804-685-1393 Phone Number – DOSWELL, VA (npnr.org).
- Report to Microsoft: Head to the Microsoft Report a Technical Support Scam Site. Make sure to incorporate the information obtained from the lookup above. Provide as much detail as possible.
- 804 Area Code Awareness: Remember, the 804 Area Code has earned a reputation as one of the leading sources of scam phone calls nationwide. While not every number within the area code is fraudulent, it’s essential to recognize the prevalent issue associated with it.
By promptly reporting suspicious numbers and potential scams, you contribute to safeguarding yourself and others from deceitful activities.
Understanding Clop Ransomware Mitigation Exploit 2: Hacks Software Applications used regularly with hidden malware.
The Clop ransomware is a type of malicious software that hackers hide in unsuspecting retail software. The cyber fraud criminals use the malicious code hidden in unsuspecting software to exploit enterprise and consumer computer, access, files and demand money to unlock them. Here are a few examples of the recent cases where hackers used sql tricks to take control of software or computers.
Understanding Clop Ransomware Mitigation MOVEit Transfer Breach
Progress Software program, MOVEit Transfer, helps people securely transfer files from one place to another. But hackers found a secret way to get into this program using a trick called an “SQL injection.” It’s like finding a hidden door that wasn’t locked properly. This secret door is a weakness that the software company didn’t know about. By using this trick, the hackers could get inside and cause trouble. This allowed them to do bad things to people’s files and ask for money to make things right.
GoAnywhere Computer Breach: Understanding Clop Ransomware Mitigation
Fortra’s GoAnywhere Computer Remote Control Breach: Fortra, has a program called GoAnywhere that also helps with secure file transfers. The hackers discovered a special kind of problem (a “vulnerability”) in this program. This problem was like a hole in a wall that the hackers could use to sneak inside. They used this hole to do things they weren’t supposed to do, like controlling the program from far away. It’s like they got the keys to a remote control for someone else’s computer. This gave them power to mess with the program and lock up files.
Software Application Developers must find and fix SQL Injection
It’s important for software companies to find and fix SQL Injection problems quickly so that hackers can’t use these tricks to cause harm to the unknowing consumers of everyday software.
Consumer Cybersecurity: Protection from Malware Attacks
In the digital realm, bolstering cybersecurity is essential for both enterprises and consumers. Safeguarding software and systems against the threat of malware and virus attacks demands a proactive approach. Employ these practices to fortify your defenses:
Regular Software Updates: Keeping Vulnerabilities at Bay
Regularly update operating systems, applications, and software with the latest security patches. This vital step closes potential vulnerabilities that attackers may exploit.
Enable Automatic Updates: Swift Action against Threats
Configure systems to receive automatic updates. This ensures that critical security patches are swiftly applied, minimizing exposure to potential threats.
Use Trusted Sources: Steer Clear of Malicious Content
Download software exclusively from official and reputable sources. Avoid unverified websites to prevent the distribution of malicious software.
Install Antivirus and Antimalware Software: Detecting and Defending
Deploy reputable antivirus and antimalware software to identify and thwart known threats from infiltrating your systems.
Firewalls and Intrusion Detection Systems: Vigilance in Network Defense
Leverage firewalls and intrusion detection systems to monitor network traffic and block unauthorized access attempts.
Secure Network Configurations: Strengthening Network Integrity
Configure networks securely by employing robust passwords, deactivating unnecessary services, and segmenting networks to contain breaches.
Employee Training and Awareness: A Human Shield against Threats
Educate employees on secure computing practices, instructing them to avoid clicking on suspicious links or downloading attachments from unknown sources.
Email Security: Barricading Against Phishing Attacks
Implement robust email security measures, including spam filters and advanced threat protection, to fend off phishing attacks and malware dispersion.
Regular Backups: A Safety Net for Critical Data
Consistently back up essential data to offline or cloud storage. This precaution ensures that, in the face of an attack, systems can be restored without ransom payments.
Multi-factor Authentication (MFA): Layered Protection
Introduce multi-factor authentication wherever feasible. This added layer of security restricts access, even if passwords are compromised.
Security Awareness Training: Empowering Vigilance
Conduct routine cybersecurity awareness training for employees. Equip them with knowledge about potential threats and safe online practices.
Vulnerability Management: Proactive Weakness Eradication
Implement vulnerability scanning and assessment to pinpoint system weaknesses and address them before they become exploitable.
Incident Response Plan: Ready for Action
Develop and maintain Critical Situation Handling incident response plan that outlines actions to take in the event of a security breach, ensuring a swift and organized response.
Monitoring and Logging: Detecting Suspicious Activities
Establish robust monitoring and logging mechanisms to promptly detect and respond to anomalous activities. One favorite is Burp Suite Professional Web Security Process
Stay Informed: A Dynamic Defense Strategy
Stay updated on the latest cybersecurity threats and trends. This proactive approach equips you to shield your systems from emerging risks.
By steadfastly integrating these practices into your cybersecurity strategy, both enterprises and consumers can substantially diminish their vulnerability to malware and virus attacks. In doing so, they forge a resilient and secure digital environment.
Resources
- AI & GRC Defense Against Security-Data Breach
- “Application impact analysis: a risk-based approach..” for the Journal of Business Continuity Emergency Planning by Beth Epstein and Dawn Khan (Simmons)
- GRC Industry Reference Matrix
- Imperative: Governance Risk Compliance
- OWASP Slack
- Security and IT Glossary

Enterprise Global Cyber Fraud Prevention- Methods: Detection & Mitigation, & IS Best Practices
-
Getting Started
- AI: ServiceNow Virtual-Agent Chatbot
- BMC Remedy ITSM Reference
- Burp Suite Professional & Web Security Process
- COE for Human Resources
- Conduct A Windows-Security Scan
- Employee Journey Management ServiceNow
- Getting Started: Engagement Manager
- Introduction to Knowledge Management
- Knowledge Categorization "Find-ability"
- One-IT: Effective Ticket Handling
- Productivity Tips for Knowledge-Users
- Productivity: Service Operations Workspace
- Quick Start Guide
- Service Catalog Order Guides
- Your Next Steps
-
- Advanced Program Management
- AI: ServiceNow Virtual-Agent Chatbot
- Artificial Intelligence A-Z Glossary
- Business Process Optimization Reviews
- Category Hierarchy and Tabs Layout
- Employee Journey Management ServiceNow
- GE Change Acceleration Process
- GRC Managed Risk
- Overview: Employee Center Pro
- Productivity: Service Operations Workspace
- Proper Ticket Handling Imperative
- Public Sector Digital Services
- RIDAC: Strategic Portfolio Management
- SOX Control-Management and Attestation
-
- Articles coming soon
-
FAQs
- Best of ServiceNow Vancouver
- Chat GPT FAQS
- DevOps & Change Velocity
- Enhancing End-User Service Experience
- FAQs: Governance Risk Compliance
- How-To Import ServiceNow Stories 🚀
- Knowledge Categorization "Find-ability"
- Role of CMDB-Management Service-Owner
- Service Catalog Process FAQs
- ServiceNow IRM SOX FAQs
- Strategic Portfolio Management FAQs
- Ticket Handling Infographic FAQs
- Understanding Clop Ransomware Mitigation
- Vulnerability Response Workspace Module
- Washington ESC or Knowledge Portal?
-
- AI & GRC Defense Against Security-Data Breach
- AI and Improved Knowledgebase-Search
- AI Revolutionizes Service Management
- AutomatePro AutoTest Custom-Testing
- AutomatePro AutoTest: Getting Started
- Best of ServiceNow Vancouver
- CMDB Health Dashboard
- Comparing ServiceNow-Strategic-PM to Microsoft-PM
- Demystifying Taxonomy Categorization
- DevOps & Change Velocity
- Efficient Workday to ServiceNow Integration
- Email-to-Incident is Costly Inefficiency
- Enhancing End-User Service Experience
- Financial Services Operations
- Gamifying ITSM Excellence
- GRC Industry Reference Matrix
- Introducing Security Incident Response
- Role of CMDB-Management Service-Owner
- Service Catalog Process FAQs
- ServiceNow Executive Reporting Approaches
- ServiceNow Virtual Agent Chatbot
- SPM Gantt Chart Presentation
- Strategic Portfolio Management FAQs
- Vulnerability Response Test Plan
- Vulnerability Response Workspace Module
- Washington ESC or Knowledge Portal?
- Show Remaining Articles11 Collapse Articles
-
Glossary Reference
-
Blog
- 2021: VP Harris Inauguration Elevates Diversity and Executive Leadership
- 5-Star ITSM Solutions
- 5-Step Policy-Compliance Risk Management
- AI & GRC Defense Against Security-Data Breach
- AI Revolutionizes Service Management
- AI: Knowledge Centered Support
- ChatGPT Ethics and FTC
- CMDB Corporate Governance for Publicly Held Companies
- Community Crisis Resource Reference List
- Covid Cyber Employment Fraud: $Millions in Job Fraud, $Billions in Unemployment Fraud. Recruiters and Jobseekers Paradigm shift
- Does Post Covid Demand, "Evolve or Fold" Data Strategy?
- Financial Services Operations
- Freshwork's Multichannel vision for FreshService (ITSM)
- Gamifying ITSM Excellence
- GRC Industry Reference Matrix
- Imperative: Governance Risk Compliance
- Jobs n Career Success: Employment News
- Microsoft Teams Tripping Transcription Tenancy.
- Predictive Intelligent Situational Awareness
- Remedy to ServiceNow Migration
- Review and Approve Knowledge
- ROI: Demand AI Service Management
- Top Trends in Project Management
- Uber's Call Center Security Social Engineering Massive System Breach
- Vulnerability Remediation RACI
- Walk Up Experience- Design-To-Deliver
- World Talent Economy Forum on Global Competitiveness
- Show Remaining Articles12 Collapse Articles
-
Healthcare
-
Workday
-
Network Connectivity Solutions
-
Business Process Methodologies