Introducing Security Incident Response
Introducing Security Incident Response, (SIR). a comprehensive solution designed to streamline and enhance the management of security incidents. SIR supports organizations in efficiently handling the entire lifecycle of a security incident, from detection through to resolution. By leveraging automated workflows, robust analytics, and seamless integration capabilities, ServiceNow SIR ensures that security teams can respond quickly and effectively to threats.
Security Operations Security Incident Response State Model
The Security Operations Security Incident Response (SIR) State Model follows a structured framework designed to ensure comprehensive and effective incident management. This model integrates best practices from the National Institute of Standards and Technology (NIST) and the SysAdmin, Audit, Network, and Security (SANS) Institute, ensuring a robust approach to handling security incidents.
NIST and SANS State Alignment
Both NIST and SANS frameworks provide detailed guidelines on managing the lifecycle of security incidents. The states in the SIR process align closely with these frameworks, ensuring that every aspect of incident management is covered.
| NIST & SANS | Description |
| Draft | Information added about the security incident, not ready for work. |
| Analysis | Incident assigned and being analyzed. |
| Contain | Issue identified, working to contain and perform damage control. |
| Eradicate | Issue contained, taking steps to fix the issue. |
| Recover | Issue resolved, verifying operational readiness. |
| Review | Incident complete, performing post-incident review. |
| Closed | Incident complete, all closure information filled out. |
| Cancelled | Incident cancelled; no further action needed. |
Supported Security Operations Processes
Detection and Analysis
Firstly, ServiceNow SIR helps in the early detection and thorough analysis of security incidents. The platform integrates with various Security Information and Event Management (SIEM) tools, such as Splunk and QRadar, to automatically generate security incidents from alerts and events. This ensures that potential threats are identified promptly.
Draft Phase
When a security incident is first created, it immediately enters the Draft state. This initial phase plays a crucial role in the incident response process as it sets the foundation for subsequent actions.
Adding Essential Information
Firstly, during the Draft phase, the request initiator has the opportunity to add comprehensive information about the incident. This includes details such as the nature of the incident, initial observations, and any relevant data that can help in the analysis and containment phases.
Holding the Incident
Furthermore, the incident remains in the Draft state until it is ready to be actively worked on. This holding period ensures that all necessary preliminary information is collected and verified before the incident progresses to the next phase. It allows the request initiator to review and refine the details, ensuring accuracy and completeness.
Preparing for Action
Moreover, the Draft phase is essential for preparing the incident for action. By allowing the initiator to meticulously document the incident, the Draft phase ensures that the security team has all the information needed to analyze and address the incident effectively.
Transition to Analysis
Finally, once the incident details are thoroughly documented and reviewed, the incident transitions out of the Draft state and into the Analysis state. This transition marks the readiness of the incident for detailed investigation and response actions by the security team.
In summary, the Draft phase is a pivotal step in the Security Incident Response process, providing a structured and detailed foundation for managing security incidents effectively.
Analysis Phase
Initiating the Analysis Phase
Once the incident is ready for action, it immediately moves into the Analysis state. Here, the incident gets assigned to an analyst who proactively investigates the issue. The analyst gathers relevant information and determines the nature and impact of the incident. This phase is crucial for understanding the full scope and severity of the incident.
Containment Phase
Active Containment Measures
Subsequently, once a security incident is identified, ServiceNow SIR assists in actively containing the threat to prevent further damage. It provides essential tools to isolate affected systems, apply emergency measures, and minimize the incident’s impact. This containment phase is vital for limiting the scope and magnitude of the incident.
Eradication Phase
Eliminating the Root Cause
Furthermore, the eradication process involves actively removing the root cause of the incident. ServiceNow SIR guides security teams through the necessary steps to eliminate malware, close vulnerabilities, and secure compromised systems. This phase ensures that the threat is completely neutralized, preventing recurrence.
Recovery Phase
Restoring Systems and Operations
Following eradication, ServiceNow SIR supports the recovery phase by helping to restore systems and operations to normal. It facilitates the implementation of recovery plans, ensuring that all systems are fully operational and secure before returning to regular use. This phase is essential for resuming normal business activities safely.
Review and Post-Incident Activity
Learning and Improvement
Finally, the review phase is crucial for continuous learning and improvement. ServiceNow SIR includes tools for conducting thorough post-incident reviews, documenting lessons learned, and updating processes and policies to prevent future incidents. This continuous improvement cycle significantly enhances the organization’s overall security posture, ensuring preparedness for future threats.
Security Incident Response Overview
Security Incident Response (SIR) manages the lifecycle of a security incident from creation through analysis, containment, eradication, recovery, and review. A security incident can include any suspected or actual threat of unauthorized access, use, disclosure, breach, or modification of information.
How Security Incidents are Initiated
Manual Initiation
Firstly, security incidents can be initiated manually. This method involves direct user intervention to create a security incident. For example:
From the Security Incident List View or Module:
Security analysts can click the ‘Create New’ button to manually enter details and create a new security incident.
From Related Records:
Users can generate a security incident from an Incident, Vulnerability, Vulnerable Item, or Alert record by clicking the ‘Create Security Incident’ button. This feature allows for quick escalation when a user identifies a potential security threat within other modules.
From the Security Incident Service Catalog:
Employees can use a predefined catalog item to report a security issue, prompting the creation of a new security incident record.
Manual Execution Example Use Case:
A security analyst notices unusual activity when reviewing the Vulnerabilities Management Workspace in a system log and manually creates a security incident from the Security Incident list view. By documenting the details, the analyst ensures that the incident is tracked and managed according to the organization’s security protocols.
- From the Security Incident list view or module (‘Create New’ button)
- From an Incident, Vulnerability, Vulnerable Item, or Alert record
- From the Security Incident Service Catalog
Automatic Initiation
Secondly, security incidents can be initiated automatically. This method uses predefined rules and integrations to create incidents without manual input. For instance:
From Alerts or Events:
Security Information and Event Management (SIEM) systems like Splunk, ArcSight, LogRhythm, or QRadar actively generate security incidents based on specific alerts or events. This integration ensures that potential threats are quickly identified and documented.
From Email:
Security incidents can be created through inbound actions, such as Security Operations Email Parsers or user-reported phishing emails. This automation helps in quickly addressing threats reported via email.
Automated Example Use Case:
A SIEM system detects an unusual pattern of failed login attempts across multiple accounts. Based on predefined rules, the system automatically generates a security incident in ServiceNow. This incident is immediately assigned to the appropriate security team for investigation, ensuring a rapid response to the potential threat.
Summary of Security Incident Response Primary Roles and Responsibilities
In the Security Incident Response (SIR) process, each role plays a crucial part in ensuring effective and timely incident management. Understanding these roles and their responsibilities is essential for seamless operation. Consequently, the following summary introduces the RACI matrix that outlines who is Responsible, Accountable, Consulted, and Informed for each task.
RACI Matrix for ServiceNow Security Incident Response (SIR)
The RACI matrix below clearly defines who is Responsible, Accountable, Consulted, and Informed for each task within the SIR process, ensuring clarity activity, task assignment, and efficiency in role execution.

Key
- R = Responsible (those who do the work to achieve the task)
- A = Accountable (the one ultimately answerable for the correct and thorough completion of the deliverable or task)
- C = Consulted (those whose opinions are sought)
- I = Informed (those who are kept up-to-date on progress)
Security Incident Response Process with New Features in Washington
Overview of the SIR Process
Firstly, the Security Incident Response (SIR) process encompasses the entire lifecycle of a security incident, ensuring that organizations can efficiently detect, contain, eradicate, recover from, and review security threats. This comprehensive process enables security teams to respond promptly and effectively to incidents, thereby minimizing potential damage.
New Features in the Washington DC Release
Introduction to the Security Incident Response Playbook
In the latest Washington DC release, ServiceNow introduces the new Security Incident Response Playbook. This innovative feature brings best practices into the Security Incident Response process, specifically designed for Security Operation Centers (SOC).
Out-of-the-Box Playbooks
Firstly, analysts can use pre-configured playbooks right out of the box. These playbooks incorporate industry best practices, ensuring that even newly established SOCs can immediately implement effective incident response strategies.
Customizable Playbooks
Moreover, the new release allows organizations to create custom playbooks tailored to their unique environments. This flexibility ensures that specific organizational requirements and unique threat landscapes are addressed comprehensively.
Enhanced User Experience
Additionally, the Washington DC release focuses on enhancing the user experience. The updated playbooks feature intuitive interfaces and streamline workflows, enabling analysts to efficiently manage and respond to security incidents.
Enabling Analysts with the New Playbook Process
Initiating the Playbook Process
Firstly, the Security Incident Response (SIR) Playbook process begins when new security incidents are generated. This initiation is crucial as it sets the stage for a structured and efficient response to potential threats.
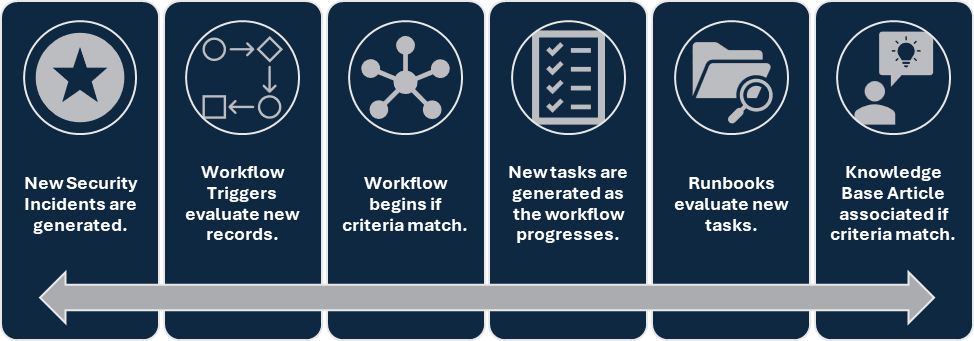
Workflow Trigger and Evaluation
Secondly, the SIR Workflow actively triggers an evaluation of new records for categorization. This evaluation ensures that analysts appropriately categorize each security incident based on predefined criteria. Such categorization is essential for determining the correct response strategy and ensuring effective incident management.
Workflow Criteria Matching
Moreover, the workflow begins in earnest when the security incident matches the workflow criteria of the playbook’s vast reference structure. This critical step ensures that the system processes only relevant incidents through the appropriate playbook, thereby streamlining response efforts and enhancing efficiency.
Task Generation
As the workflow progresses, it automatically generates new tasks. These tasks guide analysts through each step of the incident response process, ensuring that they do not overlook any critical actions. This automation plays a pivotal role in maintaining a thorough and organized response.
Automated Assistance with Runbooks
Furthermore, the integration of Runbooks significantly enhances analysts’ capabilities. Runbooks automatically help analysts evaluate new tasks by providing knowledge base article guidance based on specific criteria. This feature proves particularly beneficial, as it delivers context-specific information and instructions, empowering analysts to make informed decisions quickly.
Providing Knowledge Base Article Guidance
Additionally, the Runbooks link relevant knowledge base articles to the tasks based on specific criteria. This guidance ensures that analysts have immediate access to detailed information and best practices, enabling them to address incidents effectively and efficiently.
Enhancing Efficiency and Consistency
Moreover, the structured nature of the playbook process enhances both efficiency and consistency in incident response. By following predefined workflows and utilizing automated tools, analysts can respond to incidents in a standardized manner. This approach reduces variability and improves the overall quality of the response.
Continuous Improvement and Learning
Lastly, the playbook process actively supports continuous improvement and learning. As analysts complete tasks and resolve incidents, they can update the knowledge base and refine the playbooks. This ongoing refinement ensures that the organization continually adapts and improves its incident response capabilities.
Security Incident Response Workspace
The updated Security Incident Response Workspace has a modernized look using the ServiceNow Next Experience UI. It allows analysts to efficiently triage, own, investigate, and remediate a security incident for the entire lifecycle from start to completion.
Process Overview
States in any ServiceNow application serve a specific purpose, indicating where a record resides in a process and displaying progress.
- Detection and Analysis: Identify security events and perform initial assessment.
- Containment: Limit the scope and magnitude of a security incident.
- Eradication: Eliminate attacker artifacts and fix issues.
- Recovery: Restore impacted systems to normal operation.
- Review/Post Incident Activity: Document lessons learned and improve incident-handling capabilities.
Measurement and Governance
Process KPIs
- Mean Time to Recovery: Time from entering Analysis phase to leaving Recovery phase.
- Mean Time to Contain: Time from entering Analysis phase to leaving Contain phase.
- Mean Time to Analysis: Time from initial security incident creation to entering Analysis phase.
- Incidents Worked per Analyst by Severity: Average number of incidents worked per analyst by severity.
Security Incident Response Performance Analytics Solutions
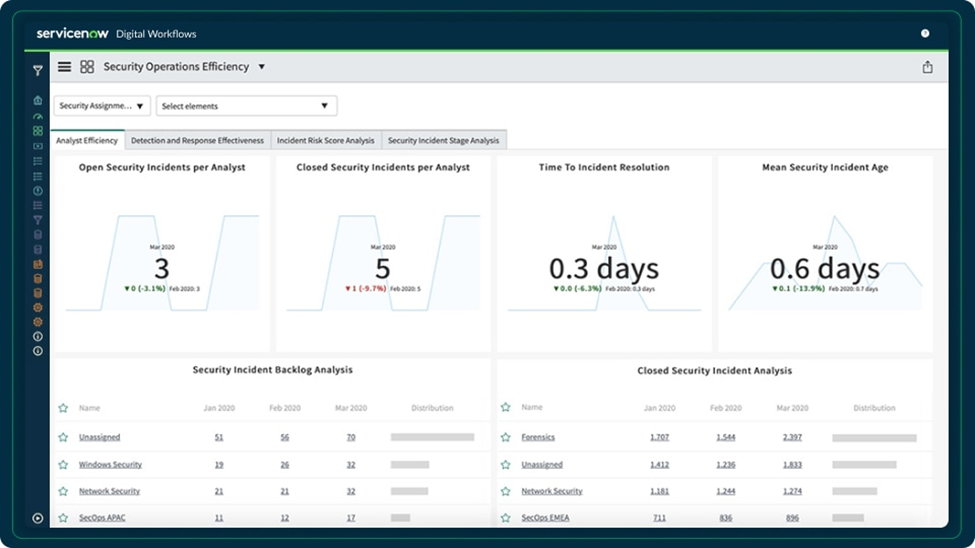
Performance Analytics Solutions contain preconfigured dashboards for analyzing the SIR process.
Dashboard views include:
- CISO Dashboard: Reveals overall security posture.
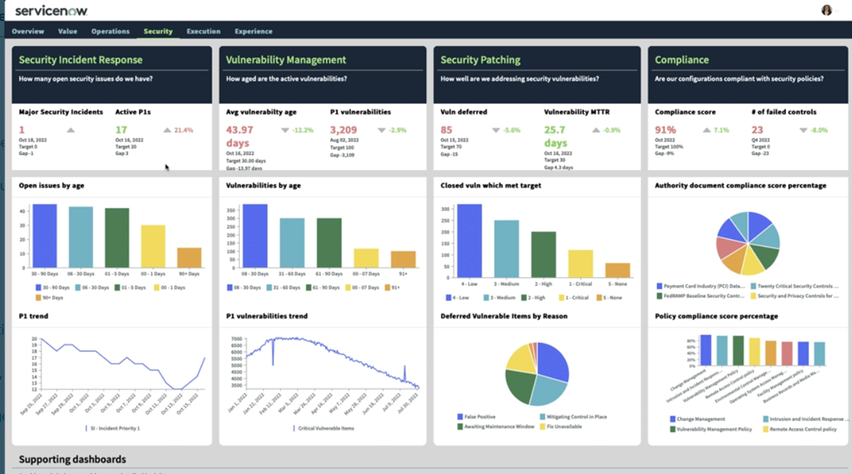
Security Incident Management Dashboard:
Tracks volume, performance, and progress of security incidents.
- Security Incident Explorer Dashboard: Summarizes incidents by category, location, priority, and business impact.
- Security Operations Efficiency Dashboard: Measures SOC team performance and efficiency.
Security Incident Calculators
Security incident calculators update record values when predefined conditions are met. Calculator groups determine how records are updated, aiding in prioritizing security incident work for analysts.
Updating Record Values
Firstly, security incident calculators play a crucial role in updating record values when predefined conditions are met. These calculators ensure that incident data remains accurate and up-to-date, providing a solid foundation for effective incident management.
Role of Calculator Groups
Moreover, calculator groups determine how records are updated. By grouping calculators based on specific criteria, ServiceNow SIR ensures that updates are consistent and relevant, aiding in the prioritization of security incident work for analysts.
Prioritizing Security Incident Work
Furthermore, these calculators aid in prioritizing security incident work for analysts. By automatically updating records based on predefined conditions, calculators help analysts focus on the most critical tasks, improving efficiency and effectiveness in incident response.
Enhancing Incident Management
Additionally, security incident calculators enhance incident management by providing automated and consistent updates. This automation reduces the likelihood of errors and ensures that all incident data is handled uniformly.
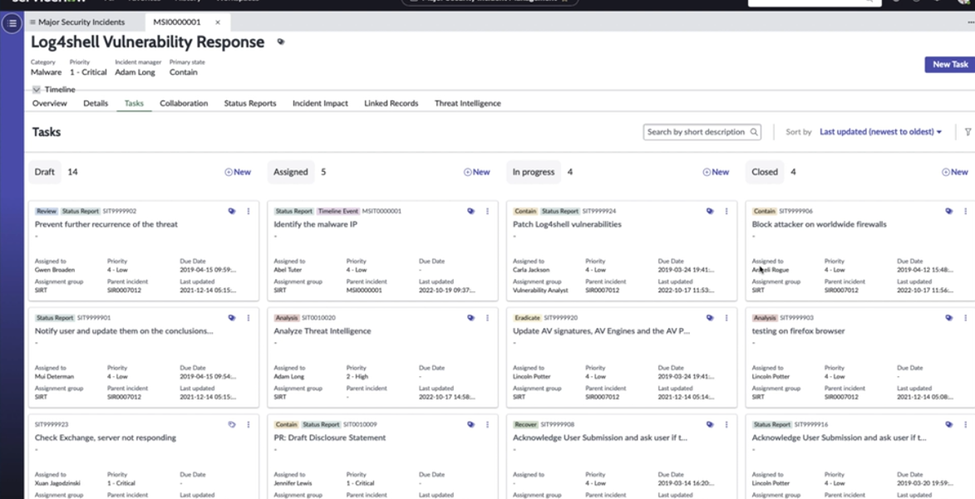
Major Security Incident Management
Firstly, ServiceNow’s SIR Major Incident Management function plays a crucial role in handling and resolving major security incidents. This powerful feature tracks and manages all activities related to significant security events, ensuring a comprehensive and coordinated response.
Proposing Major Incidents
Immediately, the function allows users to propose major incidents. By identifying critical threats early, organizations can ensure that these incidents receive the attention they require.
Promoting and Linking Incidents
Moreover, users can promote and link related incidents. This capability ensures that all connected events are managed together, providing a holistic view of the security landscape and facilitating more effective incident resolution.
Rejecting Non-Critical Incidents
Furthermore, the Major Incident Management function enables the rejection of non-critical incidents. By filtering out less significant events, security teams can focus their efforts on the most pressing threats, thereby optimizing resource allocation.
Collaborating Through the Major Security Incident Response Workspace
Additionally, the function fosters collaboration through the Major Security Incident Response Workspace. This dedicated space allows teams to coordinate activities, share information, and work together seamlessly to resolve incidents.
Enhancing Incident Management Efficiency
Consequently, the Major Incident Management function significantly enhances incident management efficiency. By providing structured processes and collaborative tools, it ensures that major incidents are handled swiftly and effectively, minimizing impact and ensuring rapid resolution.
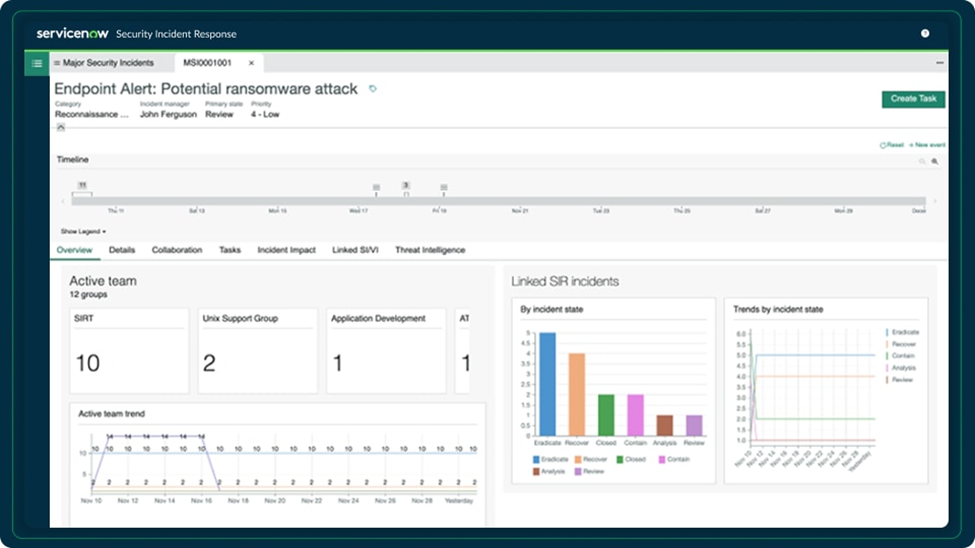
Purpose
Tracking and Managing Activities
Firstly, ServiceNow’s SIR tracks and manages activities for resolving major security incidents. This comprehensive approach includes proposing, promoting, linking, and rejecting major incidents. Additionally, it facilitates collaboration on all related activities through the Major Security Incident Response Workspace.
Threat Intelligence
Collecting and Storing STIX Data
Furthermore, the Threat Intelligence (TI) application allows users to actively collect and store STIX data. By efficiently managing this structured threat information, organizations enhance their ability to understand and respond to cyber threats.
Identifying Indicators of Compromise (IoC)
Moreover, the TI application enables users to identify Indicators of Compromise (IoC) effectively. By pinpointing these critical signs of intrusion, security teams can take swift action to mitigate threats and protect their systems.
Enriching Observables with Relevant Information
Additionally, the TI application enriches observables with relevant information. This enrichment process provides security teams with valuable context, allowing for more informed decision-making and prioritization of responses.
Integrating with the MITRE ATT&CK Framework
Importantly, the TI application integrates seamlessly with the MITRE ATT&CK framework. This integration significantly enhances threat analysis and response capabilities by aligning observed behaviors with known adversary tactics, techniques, and procedures.
Enhancing Threat Analysis and Response
As a result, organizations greatly improve their threat analysis and response capabilities. By leveraging the detailed insights from the MITRE ATT&CK framework, security teams can proactively defend against sophisticated cyber threats and maintain a robust security posture.
Integrating MITRE ATT&CK with ServiceNow SIR and Threat Intelligence
Understanding the MITRE ATT&CK Framework
Firstly, the MITRE ATT&CK framework, a globally recognized knowledge base, details the tactics, techniques, and procedures (TTPs) used by cyber adversaries. This comprehensive resource provides invaluable insights into adversary behaviors and methodologies.
Enhancing Threat Detection and Analysis
By integrating MITRE ATT&CK with ServiceNow’s Security Incident Response (SIR) and Threat Intelligence, organizations immediately enhance their threat detection and analysis capabilities. This integration allows security teams to actively correlate security incidents with specific adversary behaviors, providing a clearer picture of potential threats.
Correlating Security Incidents with Adversary Behaviors
Moreover, this integration empowers security teams to correlate security incidents with the detailed adversary behaviors outlined in the MITRE ATT&CK framework. By doing so, teams can identify patterns and techniques used in attacks, thereby improving their ability to respond effectively.
Enriching Threat Intelligence with Contextual Data
Additionally, the integration enriches threat intelligence with contextual data. This enrichment helps security teams prioritize responses based on a comprehensive understanding of the threat landscape. By having access to detailed context, teams can make more informed decisions and allocate resources more efficiently.
Proactively Defending Against Sophisticated Cyber Threats
Furthermore, organizations can proactively defend against sophisticated cyber threats through this enhanced integration. By leveraging the detailed insights provided by the MITRE ATT&CK framework, security teams can anticipate potential attack vectors and implement preemptive measures.
Improving Overall Security Posture
As a result of this integration, organizations significantly improve their overall security posture. By continuously updating their understanding of adversary tactics and integrating this knowledge into their security processes, they stay ahead of emerging threats and maintain robust defenses.

SIR Process Continuous Improvement
Facilitating Continuous Improvement and Adaptation
Firstly, ServiceNow SIR allows organizations to facilitate continuous improvement and adaptation. By leveraging the Workflow Designer, organizations can regularly review and update their workflows. This ongoing review process is crucial for incorporating new best practices, addressing emerging threats, and refining response strategies. Consequently, this adaptability ensures that the incident response process remains highly effective and consistently up-to-date in a constantly evolving threat landscape.
Identifying Areas for Improvement
To begin with, organizations must actively identify areas for improvement within their security incident response process. By conducting regular assessments and reviews of past incidents, security teams can pinpoint inefficiencies, recurring issues, and potential gaps in their current workflows. This proactive approach allows for timely adjustments and enhancements.
Automating Security Incident Response
Moreover, ServiceNow SIR empowers organizations to continuously automate their security incident response. Automation plays a critical role in reducing manual efforts, accelerating response times, and minimizing human error. By utilizing the Workflow Designer, organizations can automate repetitive tasks, streamline incident assignments, and ensure consistent application of response protocols.
Implementing Best Practices
Furthermore, implementing best practices is essential for continuous improvement. Organizations should stay informed about the latest developments in cybersecurity and incident response. By integrating these best practices into their workflows, organizations can enhance their response capabilities and ensure that their security measures align with industry standards.
Leveraging Data and Analytics
Additionally, leveraging data and analytics is vital for ongoing improvement. ServiceNow SIR provides robust analytics tools that allow organizations to analyze incident trends, performance metrics, and response effectiveness. By using this data, organizations can make informed decisions, identify patterns, and implement targeted improvements.
Training and Development
Another key aspect of continuous improvement is ongoing training and development for security teams. By regularly updating training programs and providing opportunities for skill development, organizations can ensure that their teams are equipped with the latest knowledge and techniques in incident response. This continuous learning approach enhances the overall effectiveness of the security team.
Collaboration and Feedback
Finally, fostering collaboration and feedback within the organization is crucial. Encouraging open communication between IT and security teams, as well as other stakeholders, helps in identifying improvement opportunities and implementing effective changes. By creating a culture of continuous feedback and collaboration, organizations can drive sustained improvements in their security incident response process.
Firstly, ServiceNow SIR actively leverages the Workflow Designer to streamline incident management. This powerful tool allows organizations to create, customize, and manage workflows that significantly enhance the entire incident response process.
Automating Assignments
Immediately, the Workflow Designer automates assignments. As soon as an incident is detected, the workflow promptly assigns the incident to the appropriate personnel. This action ensures that every incident receives immediate attention from the right team members, thereby eliminating delays and significantly reducing response times.
Coordinating Incident Prioritization
Moreover, ServiceNow SIR workflows play a crucial role in coordinating incident prioritization. The workflows dynamically assess the severity and potential impact of each incident, assigning a priority level based on predefined criteria. This prioritization ensures that the most critical incidents are addressed first, thereby optimizing resource utilization and enhancing the overall effectiveness of the response.
Streamlining Remediation Across IT and Security
Furthermore, workflows automate the coordination of remediation efforts across IT and security teams. By clearly defining the steps required to resolve each type of incident, workflows ensure that both IT and security teams work in perfect unison. This collaboration is essential for addressing all aspects of an incident, from technical fixes to security patches, thereby ensuring comprehensive and thorough remediation.
Enhancing Efficiency with Automated Processes
Additionally, the automated processes within ServiceNow SIR workflows significantly enhance operational efficiency. Tasks that typically require manual intervention are now automated, reducing the burden on staff and allowing them to focus on more complex and strategic activities. This automation not only accelerates the incident response process but also minimizes the likelihood of human error.
Ensuring Consistency and Compliance
ServiceNow SIR workflows also ensure consistency and compliance in incident response. By adhering to predefined procedures and guidelines, the workflows help organizations comply with industry standards and regulatory requirements. This consistency is crucial for maintaining a high level of security and ensuring that all incidents are handled in a uniform and compliant manner.
Facilitating Continuous Improvement and Adaptation
Finally, the Workflow Designer allows for continuous improvement and adaptation. Organizations can regularly review and update their workflows to incorporate new best practices, address emerging threats, and refine their response strategies. This continuous adaptability ensures that the incident response process remains highly effective and consistently up-to-date in a constantly evolving threat landscape.
Summary
In summary, ServiceNow SIR’s approach using the Workflow Designer and automated workflows revolutionizes incident management. By automating assignments, coordinating prioritization, and streamlining remediation efforts, these workflows enhance efficiency, ensure consistency, and facilitate continuous improvement, ultimately leading to a more effective and resilient security posture.
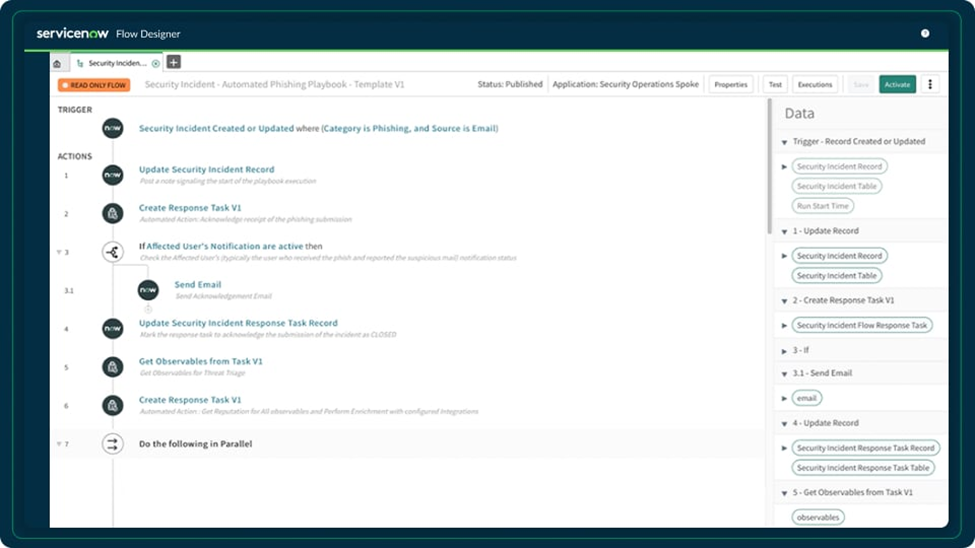
Reference Information
-
Getting Started
- AI: ServiceNow Virtual-Agent Chatbot
- BMC Remedy ITSM Reference
- Burp Suite Professional & Web Security Process
- COE for Human Resources
- Conduct A Windows-Security Scan
- Employee Journey Management ServiceNow
- Getting Started: Engagement Manager
- Introduction to Knowledge Management
- Knowledge Categorization "Find-ability"
- One-IT: Effective Ticket Handling
- Productivity Tips for Knowledge-Users
- Productivity: Service Operations Workspace
- Quick Start Guide
- Service Catalog Order Guides
- Your Next Steps
-
- Advanced Program Management
- AI: ServiceNow Virtual-Agent Chatbot
- Artificial Intelligence A-Z Glossary
- Business Process Optimization Reviews
- Category Hierarchy and Tabs Layout
- Employee Journey Management ServiceNow
- GE Change Acceleration Process
- GRC Managed Risk
- Overview: Employee Center Pro
- Productivity: Service Operations Workspace
- Proper Ticket Handling Imperative
- Public Sector Digital Services
- RIDAC: Strategic Portfolio Management
- SOX Control-Management and Attestation
-
- Articles coming soon
-
FAQs
- Best of ServiceNow Vancouver
- Chat GPT FAQS
- DevOps & Change Velocity
- Enhancing End-User Service Experience
- FAQs: Governance Risk Compliance
- How-To Import ServiceNow Stories 🚀
- Knowledge Categorization "Find-ability"
- Role of CMDB-Management Service-Owner
- Service Catalog Process FAQs
- ServiceNow IRM SOX FAQs
- Strategic Portfolio Management FAQs
- Ticket Handling Infographic FAQs
- Understanding Clop Ransomware Mitigation
- Vulnerability Response Workspace Module
- Washington ESC or Knowledge Portal?
-
- AI & GRC Defense Against Security-Data Breach
- AI and Improved Knowledgebase-Search
- AI Revolutionizes Service Management
- AutomatePro AutoTest Custom-Testing
- AutomatePro AutoTest: Getting Started
- Best of ServiceNow Vancouver
- CMDB Health Dashboard
- Comparing ServiceNow-Strategic-PM to Microsoft-PM
- Demystifying Taxonomy Categorization
- DevOps & Change Velocity
- Efficient Workday to ServiceNow Integration
- Email-to-Incident is Costly Inefficiency
- Enhancing End-User Service Experience
- Financial Services Operations
- Gamifying ITSM Excellence
- GRC Industry Reference Matrix
- Introducing Security Incident Response
- Role of CMDB-Management Service-Owner
- Service Catalog Process FAQs
- ServiceNow Executive Reporting Approaches
- ServiceNow Virtual Agent Chatbot
- SPM Gantt Chart Presentation
- Strategic Portfolio Management FAQs
- Vulnerability Response Test Plan
- Vulnerability Response Workspace Module
- Washington ESC or Knowledge Portal?
- Show Remaining Articles11 Collapse Articles
-
Glossary Reference
-
Blog
- 2021: VP Harris Inauguration Elevates Diversity and Executive Leadership
- 5-Star ITSM Solutions
- 5-Step Policy-Compliance Risk Management
- AI & GRC Defense Against Security-Data Breach
- AI Revolutionizes Service Management
- AI: Knowledge Centered Support
- ChatGPT Ethics and FTC
- CMDB Corporate Governance for Publicly Held Companies
- Community Crisis Resource Reference List
- Covid Cyber Employment Fraud: $Millions in Job Fraud, $Billions in Unemployment Fraud. Recruiters and Jobseekers Paradigm shift
- Does Post Covid Demand, "Evolve or Fold" Data Strategy?
- Financial Services Operations
- Freshwork's Multichannel vision for FreshService (ITSM)
- Gamifying ITSM Excellence
- GRC Industry Reference Matrix
- Imperative: Governance Risk Compliance
- Jobs n Career Success: Employment News
- Microsoft Teams Tripping Transcription Tenancy.
- Predictive Intelligent Situational Awareness
- Remedy to ServiceNow Migration
- Review and Approve Knowledge
- ROI: Demand AI Service Management
- Top Trends in Project Management
- Uber's Call Center Security Social Engineering Massive System Breach
- Vulnerability Remediation RACI
- Walk Up Experience- Design-To-Deliver
- World Talent Economy Forum on Global Competitiveness
- Show Remaining Articles12 Collapse Articles
-
Healthcare
-
Workday
-
Network Connectivity Solutions
-
Business Process Methodologies
