CMDB Health Dashboard
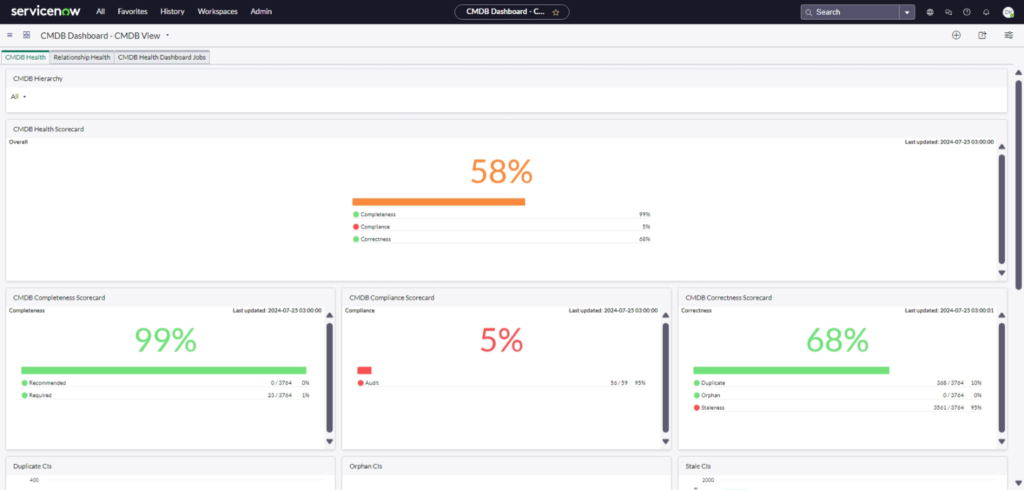
CMDB Health Dashboard: Why It Is So Critical to Enterprise Management, Security, ITSM, and ServiceNow
The CMDB Health Dashboard is a cornerstone for effective enterprise management. It provides a comprehensive view of your configuration data’s accuracy, completeness, and compliance, ensuring that your IT infrastructure is both reliable and secure. For enterprise management, it offers critical insights that help streamline operations and improve decision-making. From a security standpoint, a healthy CMDB minimizes vulnerabilities by maintaining up-to-date and accurate configuration data. In the realm of IT Service Management (ITSM), the CMDB Health Dashboard enhances service delivery by ensuring all assets and their relationships are correctly documented and managed. Overall, the CMDB Health Dashboard is an indispensable tool in ServiceNow, driving efficiency, security, and excellence in IT operations.
AutoTest Case Planning

AutoTest Case Planning is essential for efficient test automation with AutomatePro. Learn how to organize and convert existing test records, develop automated tests from acceptance criteria, and manage testing for new users and product upgrades. This guide covers identifying personas, mapping high-level process flows, grouping tests for maximum efficiency, and providing ongoing support, ensuring robust test coverage for your projects.
Quality Assurance Test Process

Quality Assurance Test Process: Ensuring Excellence from Story to Production
Welcome to the AutomatePro AutoTest for ServiceNow Products. Our QA Test Process guides for moving stories from inception to production, covering all critical QA activities, including planning, designing test cases, unit testing, running story tests, managing defects, and conducting production smoke testing, while emphasizing comprehensive documentation and best practices.
Autotest: Test-Run Defects

Autotest: Test-run defects are an important part of the testing process, but understanding and addressing the common causes can significantly improve your testing outcomes. By systematically addressing navigation failures, element not found errors, timing issues, and data dependencies, you can ensure more reliable and successful test runs with AutomatePro Autotest.
AutomatePro AutoTest Custom-Testing

AutomatePro AutoTest Custom-Testing allows you to tailor your automated testing processes to meet specific requirements within ServiceNow. By leveraging custom actions and checks, you can define precise interactions and validations that go beyond standard testing capabilities. This guide will introduce you to the essential concepts of custom-testing, including creating and configuring custom actions, using XPath and CSS selectors, and handling complex web elements like frames and shadow roots. Whether you are new to automated testing or looking to enhance your current setup, this comprehensive overview will equip you with the knowledge to optimize your testing workflow.
AutomatePro AutoTest: Getting Started

AutomatePro AutoTest: Getting Started: Discover how AutomatePro AutoTest can revolutionize your ServiceNow testing process, making it more efficient and reliable. This guide provides essential steps to get you started with creating, executing, and managing automated tests, ensuring your business processes are thoroughly tested and maintained.
AutomatePro AutoTest Reference

AutomatePro AutoTest Reference: start to automate your testing processes, for more efficient and reliable results. For more detailed information, refer to the comprehensive AutomatePro documentation. Happy testing!
DevOps Automated Test

DevOps Automated Test to discover the critical importance of automation in Agile testing in ensuring high-quality software delivery, from story grooming to production, with clear responsibilities and a seamless DevOps process. This guide offers essential insights into Agile testing foundations, a detailed RACI matrix, and a high-level workflow to enhance your development and deployment efficiency.
Vulnerability Response Test Plan

Vulnerability Response Test Plan follows a structured approach with the relevant personas and type of tests to perform a comprehensive assessment of the ServiceNow Vulnerability Response module’s readiness for implementation.
Introducing Security Incident Response
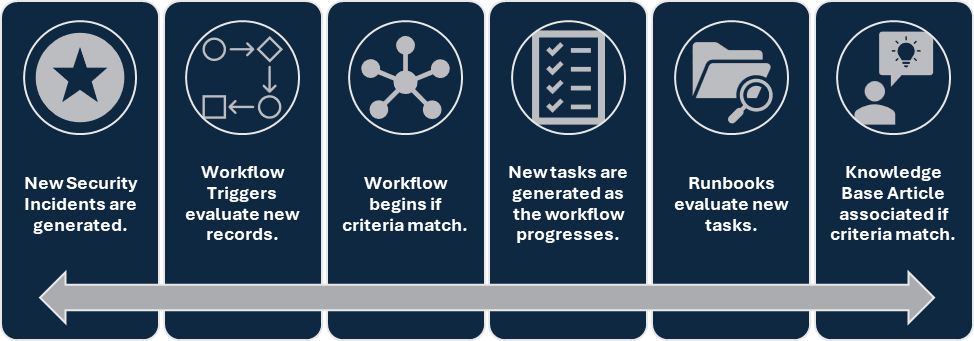
Introducing Security Incident Response (SIR), a comprehensive solution designed to streamline and enhance the management of security incidents. SIR empowers organizations to efficiently handle the entire lifecycle of a security incident, from detection to resolution. By leveraging automated workflows, robust analytics, and seamless integration capabilities, ServiceNow SIR ensures that security teams respond quickly and effectively to threats.
