Vulnerability Remediation RACI

Vulnerability Remediation Process RACI: Empowering Security Excellence
In the ever-evolving landscape of cybersecurity threats, organizations face a constant battle to safeguard their digital assets and sensitive information. The Vulnerability Remediation Process, armed with a potent RACI matrix, emerges as a strategic weapon in this ongoing war. It doesn’t just manage vulnerabilities; it orchestrates security excellence.
Responsible, Accountable, Consulted, and Informed—these four simple words encapsulate the essence of a process that can be the difference between resilience and vulnerability, between security and chaos. Let’s embark on a journey through this dynamic framework, where precision and collaboration reign supreme.
Imagine the scenario: Your organization, like a fortress, relies on a multitude of interconnected systems, applications, and networks. The walls of this fortress must remain impenetrable, but vulnerabilities lurk in the shadows, waiting for that one crack in the defenses. This is where the Vulnerability Remediation Process steps into the spotlight.
Responsible individuals take charge of the initial phase, identifying these vulnerabilities, and are primarily our vigilant IT Security Team. Their keen eyes spot the weak links, their expertise classifies the threats, and they start the critical task of assessing risk. They are the first line of defense, the guardians of our digital realm.
But in a world where vulnerabilities come in all shapes and sizes, a single pair of watchful eyes is not enough. This is where the Consulted and Accountable roles shine. The Vulnerability Management Team steps up as the commanders of the operation, ensuring vulnerabilities are assessed, prioritized, and managed with strategic precision. They lead the charge, setting the course for remediation. Meanwhile, the IT Operations Team, Application Owners, and more, all Consulted in this phase, bring their unique expertise to the table. Their contributions are invaluable, ensuring a holistic approach to vulnerability management.
As the battle plan takes shape, it’s time for the Remediation Execution phase. The IT Operations Team takes the reins, wielding patches and configurations as their weapons of choice. But they don’t stand alone. They work in tandem with the Vulnerability Management Team and Application Owners, ensuring every action aligns with the strategy and minimizes disruptions.
This is just the beginning of our journey through the Vulnerability Remediation Process. Beyond this point lies validation, verification, reporting, and continuous improvement, each step carefully orchestrated, each role finely tuned. Through the RACI matrix, every contributor knows their place, their role, and their significance in the pursuit of security excellence.
Digital Security Operations is vigilant, because cyber threats never rest, the Vulnerability Remediation Process RACI sets clear tasks and roles that empowers enterprises to keep pace with cybersecurity with confidence, ensuring that our digital profile remains resilient, data remains secure, and operations resilient to the constantly emerging digital enterprise vulnerabilities.
5-Step Policy-Compliance Risk Management
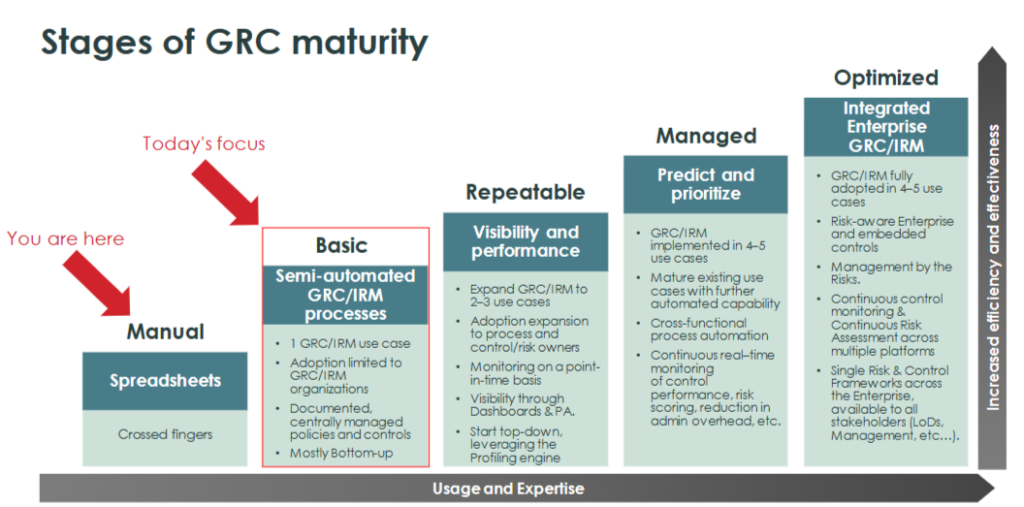
5-Step Policy-Compliance Risk Management Implementation Tips: The successful implementation of ServiceNow Policy, Compliance, and Risk Management hinges on a meticulous and structured approach. This entails a series of critical steps designed to fortify governance, achieve regulatory compliance, and fortify risk management within the organization.
Remedy to ServiceNow Migration

Remedy to ServiceNow Migration
5-Star ITSM Solutions

5 star ITSM Solutions
AI & GRC Defense Against Security-Data Breach

ServiceNow-Learning Highlights: GRC is an essential power tool to maintain a secure competitive edge, embrace innovation and remain at the forefront of technological advancements.
Walk Up Experience- Design-To-Deliver

Walk Up Experience- Design-To-Deliver: In a realm where people’s schedules are tight, the walk-up service is a key employee value. A service desk implementation of a walk-up service yields multifaceted […]
GRC Industry Reference Matrix

GRC Industry Reference Matrix: the comprehensive guide for managing regulations, risks, and standards across industries. Uncover the intricate interplay of Regulatory Focus, Risk Management, Compliance Standards, Industry Associations, Key Challenges, […]
AI Revolutionizes Service Management
AI Revolutionizes Service Management: In the realm of modern Service Management, the spotlight firmly rests on the transformative prowess of AI and Predictive Intelligence, with sound ServiceDesk Agent Support. A […]
Gamifying ITSM Excellence

Gamifying ITSM Excellence. Leveraging gamification, you can conquer prevalent ITSM challenges and attain excellence. This dynamic approach fosters shared visions, secures senior buy-in, surmounts change resistance, addresses resource constraints, and […]
Imperative: Governance Risk Compliance

Imperative: Governance Risk Compliance elevate integrity for effective management in Banking, Finance, Healthcare, and Government. GRC’s dynamic, iterative high-level process reflects continual risk and compliance activities. Collaborate, train, and commit […]

