Cyber Attack Readiness Matters: The American Medical Association elevates the voice of physicians, medical students and health care workers while highlighting developments and achievements throughout medicine. The AMA Update recently featured building resilient healthcare cyber security practice with expert, Charles Aunger, who discusses recent cyber-attacks, ransomware trends and cybersecurity threat guidance for awareness, vulnerabilities, and Threat Management.
HEAL SECURITY NEWS:
- Attacks Surge on Check Point’s Recent VPN Zero-Day Flaw
- Hackers Created Rogue VMs to Evade Detection in Recent MITRE Cyber Attack
- HHS Warns Cyberthreats Email Bombing & Credential Harvesting
- Reactions to the Ascension Healthcare Ransomware Attack and Suggestions for Healthcare
- Recent Healthcare Ransomware Attacks
Increasing Frequency and Severity of Cyber Attack Readiness Matters
Firstly, cyber breaches are happening more often and causing more damage. In 2024 alone, there have been around 20 major breaches in North America, Europe, and Japan.
- TechRadar These breaches impact governments, healthcare, and businesses worldwide, threatening organizations of all sizes. Moreover, a lack of threat monitoring, containment, and detection is a leading issue.
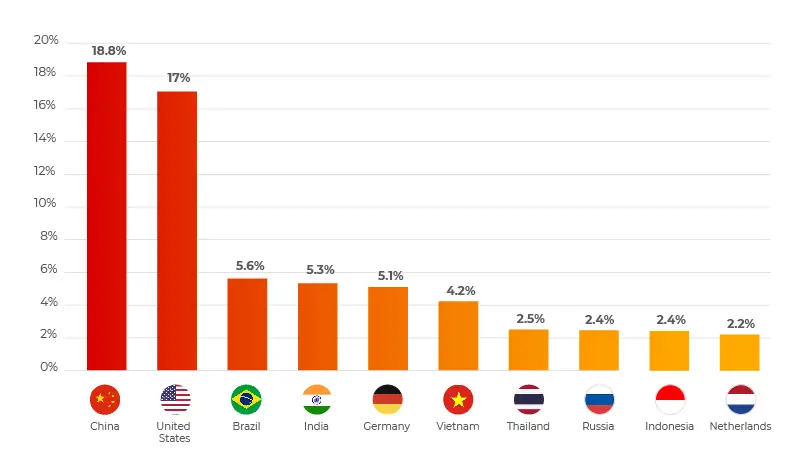
- Meanwhile, Cyber Proof identified China, the United States, Brazil, India, and Germany as the top five threat sources.
Cyber Attack Readiness Matters: Learning from 2024’s News Making Exploits.
Moreover, notable cybersecurity breaches in recent years highlight the critical importance of best practices in cybersecurity.
UnitedHealth’s $872 Million Cyberattack still rising, expected to reach $1B
In 2024, UnitedHealth Group suffered a massive ransomware attack, resulting in an $872 million loss. This breach affected their ChangeHealthcare platform, disrupting transactions between doctors, pharmacies, and healthcare professionals. A vulnerable Citrix portal was exploited, leading to the attack.
US Department of Health and Human Services is investigating whether protected health information was compromised and if Change Healthcare and UHG complied with Health Insurance Portability and Accountability Act (HIPAA) rules. It is believed that implementing rigorous security monitoring and automated incident response tools could have detected and mitigated this vulnerability early on, preventing the breach.
England and Wales Cricket Board Data Breach Cyber Attack
In March 2024, the icoachcricket platform breach, used by the England and Wales Cricket Board (ECB), impacted 40,000 users. Consequently, the IntelBroker criminal operation leaked user data, which included email addresses and hashed passwords. To prevent such breaches, implementing stronger data encryption and conducting regular security assessments could have protected this sensitive information.

AT&T Cyber Attack: Leak of more than 73 Million Customer’s Data to the Dark Web
In a staggering incident, AT&T experienced a cyber attack that led to the leak of over 73 million customers’ data to the dark web. This breach, undoubtedly one of the most significant in recent history, underscores the critical importance of robust cybersecurity measures.
Details of the Attack
Initially, cybercriminals exploited vulnerabilities in AT&T’s security infrastructure. They accessed a vast amount of customer data, including personal details such as names, addresses, phone numbers, and email addresses. Subsequently, this data was uploaded to the dark web, making it accessible to other malicious actors who could use it for various nefarious purposes, such as identity theft, phishing scams, and financial fraud.
Immediate Consequences
The immediate consequences of this attack were severe. Customers faced heightened risks of identity theft and financial loss. AT&T, on the other hand, suffered significant reputational damage and incurred substantial costs in responding to the breach and mitigating its effects.
Mitigation Strategies: What Could Have Been Done?
To prevent such a devastating breach, AT&T could have implemented several critical measures:
Strengthening Security Infrastructure
Firstly, AT&T could have strengthened its security infrastructure. By employing advanced encryption techniques, the company could have ensured that even if data were accessed, it would remain unreadable and useless to unauthorized users.
Regular Security Audits
Moreover, conducting regular security audits would have identified vulnerabilities in their systems before cybercriminals could exploit them. These audits, combined with penetration testing, would have provided insights into potential weaknesses and allowed AT&T to address them proactively.
Implementing Multi-Factor Authentication
Additionally, implementing multi-factor authentication (MFA) for accessing sensitive systems and data could have added an extra layer of security. MFA requires users to verify their identity through multiple methods, making it significantly harder for attackers to gain unauthorized access.
Continuous Monitoring and Threat Detection
Continuous monitoring and real-time threat detection systems would have enabled AT&T to detect suspicious activities early. By analyzing network traffic and identifying unusual patterns, these systems could have alerted security teams to potential breaches, allowing them to respond swiftly and mitigate the threat.
AT&T and AT&T Third Party Vendor – Employee Training and Awareness
Firstly, comprehensive employee training and awareness programs are essential for enhancing cybersecurity. These programs educate employees about the importance of cybersecurity, helping them understand the risks and their role in mitigating those risks. By being well-informed, employees can follow best practices and avoid actions that could compromise security.
Recognizing Phishing Attempts
Moreover, training programs focus on recognizing phishing attempts. Phishing is a common method used by cybercriminals to access sensitive information. By teaching employees to identify suspicious emails, links, and attachments, organizations can significantly reduce successful phishing attacks.
Following Best Practices
Furthermore, employees learn to follow cybersecurity best practices through these training programs. This includes using strong, unique passwords, enabling multi-factor authentication, and being cautious about sharing sensitive information. Following these practices helps create a secure work environment and minimizes the risk of data breaches.
Third-Party Risk Management Process
Assessing Third-Party Risks
Additionally, a robust third-party risk management process is crucial for maintaining security. This process starts with assessing the risks associated with third-party vendors. Organizations need to evaluate the security measures and protocols of their vendors to ensure they meet the required standards. This assessment helps identify potential vulnerabilities that cybercriminals could exploit.
Conducting Due Diligence
Moreover, conducting due diligence is a critical component of third-party risk management. This involves thoroughly vetting vendors before establishing a partnership. By reviewing their security policies, past incidents, and overall risk profile, organizations can make informed decisions about which vendors to work with.
Continuous Monitoring
Furthermore, continuous monitoring of third-party vendors is essential. Regular audits and assessments ensure that vendors maintain the necessary security standards throughout the partnership. This ongoing evaluation helps identify any changes in the vendor’s security posture and allows for timely intervention if any issues arise.
Implementing Security Controls
Organizations should put security measures in place to reduce third-party risks. This includes setting clear security rules in contracts, making sure vendors follow specific security protocols, and controlling access to data. These steps protect sensitive information and lower the risk of data breaches.
Trello Data Leak
Firstly, in January 2024, Trello had a big data leak that affected 15 million accounts because of weak security. A public API matched emails with Trello accounts, which exposed user data. If Trello had improved API security and required authentication, they could have prevented this leak. This incident shows why strong security measures are essential.
The Necessity of Advanced Tools
Advanced tools are crucial for strong cybersecurity as they help quickly find, control, and fix security issues. These tools let organizations respond fast to incidents. Additionally, tools with live threat information and analysis strengthen overall security.
Resources for Cyber Attack Readiness Matters
- Association of Generative Artificial Intelligence (AI)
- HEAL Security – Cyber Threat Intelligence for Healthcare Sector
- KAUST: AI-Healthcare Innovation
- Security and IT Glossary
- Security Incident Response Introduction
- SecOps Vulnerability Response Lifecycle
- Vulnerability Response


